|
|



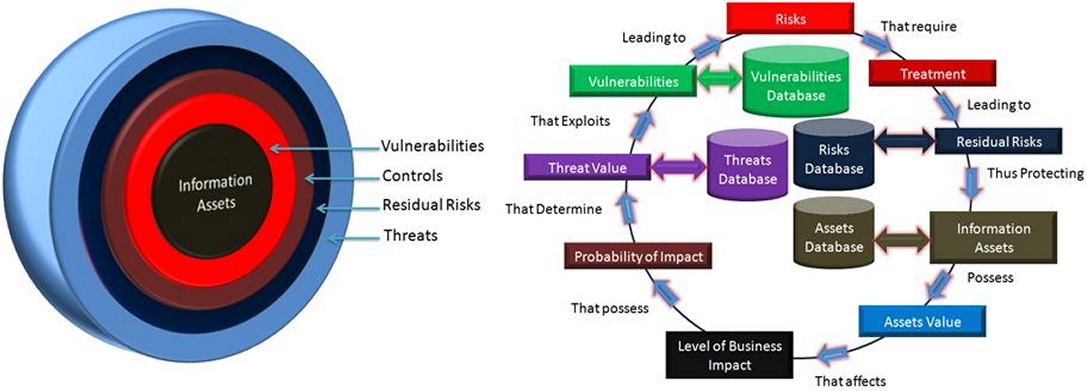
IT and Information Risk Management and Business Impact Analysis at Corporate and Enterprise Levels: The Opportunities for Academic Dissertations and Thesis Projects The standards and best practices of Information Risk Management have evolved significantly in the recent past with the evolution of cloud computing and the emerging threats to client businesses running their ICT (Information and Communication Technologies) on the clouds. Cloud computing infrastructures are massive Internet-enabled data centres having virtualised pools of computing, storage, networking, and platform resources in service-oriented configurations. Every client organisation gets a personalised Virtual Private Cloud (VPC) packaged with the desired ICT resources operating within a domain protected by virtualised boundaries. Access control to the ICT resources in the VPCs are managed through virtual cloud security controls. Two VPCs can be interconnected through VPC-to-VPC tunneling. The key challenges in this configuration are the following: (a) Most of the security controls are owned and managed by the cloud service providers. The client organisation merely gets access to controls related to users and groups management. (b) There is inadequate visibility into the threats and risks to the ICT assets of the client organisation. Simply stated, the client organisations do not have access to their respective comprehensive risks registers. (c) The clouds have a massive attack surface. If an exploit materialises successfully, thousands of businesses can be taken down by a small group of hackers. This was evident in the massive Distributed Denial of Service (DDoS) attack on DYN DNS servers on October 21 2016 that had crippled thousands of web business organisations having high dependence on cloud-based ICT resources. This attack was carried out using hundreds of thousands of compromised Internet Of Things. Despite of such a massive sttack, the client organisations could only wait and watch what DYN and the associated cloud service organisations were doing to implement preventive controls against reoccurence of this risk in future. (d) The clients are locked-in with a cloud service provider over a period. It is very difficult for a client organisation to shift the ICT resources back to self-hosted data centres or to other cloud service providers. (e) There is no common enterprise-wide risks view for the businesses. (f) The data stored on the cloud is spread across multiple unknown (untraceable) locations. There is a high risk of data proliferation with no clarity on who shall be responsible. (g) There is lack of clarity of the structure of accountability for protection of clients' ICT resources on the cloud computing. (h) Moving ICT resources to cloud computing results in dismantling of the core ICT organisational structures that companies have been maintaining for decades. In addition, the ICT services management and governance standards maintained by companies are diluted because the controls are transferred to cloud service providers. For example, companies do not have much left to manage in the areas of incident, problem, change, release, configuration, availability, service level, disaster recovery, and business continuity management. (i) The framework of Enterprise Risk Management is no longer managed and controlled by companies as majority of the risks are transferred to third parties (cloud service providers) (j) The power of Enterprise Architecture controls is gradually shifting towards cloud service providers. Please visit our page Cloud Computing and Virtualisation Risks and Controls for research topics on ICT risks and controls on the clouds. In addition to the suggestions in this article, please contact us at consulting@eproindia.com or consulting@eproindia.net to get more topic suggestions and to discuss your topic. There is a clear shift of power structures of the individual enterprises after they have adopted cloud computing. Perhaps, a roll back from this position to the power of self-hosted ICT services in future will be almost impossible amidst lack of migration platforms, lack of skilled ICT employees, lack of consultancy, and an overall lack of knowledge and expertise. One may view the current state of the cloud-dependent business organisations as an irreversible shift of organisational inertia; a change without a back-out plan. However, cloud is here to stay as hundreds of thousands of business, government, public sector, and not-for-profit organisations have moved their ICT resources to cloud computing. Hence, the approach of researchers should not be only to criticise cloud computing but also find out ways to live with it and change the ways businesses have been managing their ICT risks and security. To explore the research opportunities on cloud computing, a basic understanding of the traditional risk management standards is mandatory. I hereby discuss the Information Risk Management and Business Impact Analysis framework from the perspective of the standard ISO 27005:2008, which is based on ISO 27001:2013 (formerly ISO 27001: 2005) and ISO 27002:2008 controls. The ISO 27005:2008 standard is the formal replacement of ISO 13335-3 & ISO 13335-4:2000 which essentially recommends a 100% metrics based evaluation of all the steps of risk assessment described in ISO 13335-3 using quantitative techniques. This standard considers Risk Management, Configuration Management and Change Management as an integrated framework to deliver IT security in an organization. The risk management framework recommended by this standard can be viewed as a "concentric spheres" model with the information assets placed at the core of the model as shown in the figure below. This model was originally part of ISO 13335-3 that represents an environment of threats that change continuously thus changing the risk baselines (residual acceptable risk levels) of the organizations and hence requires periodic assessment of the effectiveness of controls such that the vulnerabilities are not exploited by the external threats to affect the information assets. Figure Description: Concentric Spheres Model of Risk Management Framework (LEFT) and the Relationships Among Various Attributes of the Information Risk Management Framework (RIGHT) (Source: ISO 27005 conceptual framework) Based on the environment of threats and resulting risks the relationships in risk management, as defined by ISO 27005 framework is presented in the figure above. A close observation of the figure shall reveal that every parameter can be assigned a metric value which can be measured objectively within a given environment. The interrelationships of these parameters will result in a matrix like structure whereby the metrics of these parameters form a relationship and hence control each other. For example, high asset value and high impact with low probability value may lead to lower threat value and hence lower risk value. Hence, in spite of high asset value and high impact, the risk treatment may not be urgent for this asset. Typical example may be - impact due to flooding to a Data Centre on the top floor of a building that is many miles away from a river and also has water storage tank located few hundred meters away from the base of the building. A threat analysis coupled with history of flooding may lead to very low probability of flooding and hence the risk value may arrive to be below the threshold of residual risks. Now let us imagine that the building authorities decided to install an overhead water tank on the roof top. In this case the probability of impact on the asset may suddenly shoot up thus increasing the risk value beyond the threshold. Now the risk will need urgent treatment by the asset owner to bring it back to the residual level below the threshold. This is the magic of metrics-based risk assessment as defined in the ISO 27005 standard. Variation of metrics would lead to variation in risk values thus changing the perspective of the risk management team related to an asset. Thus, the standard recommends metrics based relationship analysis of all parameters against every information asset identified in the organization. The analytics require various databases to be maintained by the risk management team such that the metrics analysis can be revisited periodically whereby the additions in the related databases may lead to variations demanding change in perspective of the risks identified. The databases required to manage this relationship model effectively is presented in the figure above. Dear Visitor: Please visit the page detailing SUBJECT AREAS OF SPECIALIZATION pertaining to our services to view the broader perspective of our offerings for Dissertations and Thesis Projects. Please also visit the page having TOPICS DELIVERED by us. With Sincere Regards, Sourabh Kishore. Apologies for the Interruption!! Please Continue Reading!! For cloud computing, ISO 27001: 2013 and ISO 27005:2008 have been transformed into ISO 27017:2015 and ISO 27018:2016 standards, which are the future standards of Information Security and Risk Management in the cloud computing era. Whichever organization is able to establish the trust relationships correctly will save lot of time & efforts in managing information risks and will also be able to achieve employee satisfaction because this framework ensures enormous participation by employees without needing to be specialists in IRM domain. This however is still a hypothesis and requires efforts by academic researchers to be converted into an empirical theory. Although a number of academic research studies have been conducted on these areas, they are largely inadequate because these areas have evolved and grown many times faster than the pace of researches by academicians and students. I suggest that students should undertake new topics for dissertations and theses in these areas given that a lot remains unaddressed by the academic community in the fields of Information Security Risk Management and Business Impact Analysis and Management. Now, let us discuss the risk management process in detail. Information Assets are very critical for success of modern IT enabled businesses. In the modern world, information assets are exposed to threats that have emerged as major IT security challenges. The threats to information assets result in "Risks" with potential impact to businesses. The potential damage against an impact classifies the "Criticality" of the Risk. The key to Information and IT Security of an organization is to know the assets, to know the threats to the assets, assess the probability and impacts to business, accurately measure the associated risks, and finally establish appropriate mitigation strategies to reduce, avoid or transfer the risks. I recommend that Information Risk Management should be an integral part of an organization's corporate governance such that adequate executive attention to the risks and corresponding Information and IT security controls can be invited and mitigation strategies can be formulated. In many countries, it is legally required to implement appropriate IT Security if the organization is managing critical public systems or data. Dear Visitor, Please visit the page pertaining to STANDARDS ON INFORMATION RISK MANAGEMENT AND IT GOVERNANCE. With Sincere Regards, Sourabh Kishore. Apologies for the interruption; Please continue reading!! To manage Information Risks it is mandatory to know ALL the critical information assets of the organization. Every system that creates, processes, transfers or stores information is an information asset - like, file/folders, databases, hard copy storage areas, desktops, laptops, shared network resources, employees' drawers/lockers, or the employees' own memory (tacit knowledge). The primary requirement of Risk Management is to have an "Information Asset Register" which is a secured database that needs to be updated regularly as and when new assets are added, modified or deleted. Every organization can have their own definitions of "Confidentiality", "Integrity" and "Availability" parameters related to an Information Asset. These parameters should translate into metrics that should be assigned to EVERY critical information asset identified in the Information Asset Register. The outcome is known as an "Asset Value" tagged against every asset entered in the Asset Register. The next important step is to assess the "Threat Value" by virtue of an in-depth analysis of the possible causes, the impact value (a function of multiple impacts like Financial or Reputational impact), and the probability of an impact. Every organization can have their own parameters for calculation of Threat Value because it largely depends upon the exposure factors (like Legal, Competition, Environmental, etc) that the organization is facing or can potentially face in future. The subsequent step is to assess the "Loss Event Value" which is a function of the possible events of asset compromising that the organization can face. Again every organization can have their own loss event descriptions and the assessment methodology that are normally categorised under the known vulnerabilities in the organization. The final step is to arrive at the "Risk Value" which is a function of the Asset Value, the Threat Value and the Loss Event Value. The calculation of Risk Value can be carried out differently for different organizations depending upon how many levels of escalation is feasible within the organization. Information Assets with high Risk Values have high "Vulnerabilities" and hence appropriate controls need to be applied urgently. Business Impact Analysis is the next step after completion of the Risk Assessment. Risk Assessment process will ensure that all the Information Assets of the organization are identified and the corresponding "Risk Values" are assessed. The scale of the Risk values can be defined depending upon the number of escalations feasible within an organization. A large organization may like to keep a larger scale of Risk Values leading to more levels of escalation such that minor risks are not un-necessarily escalated to senior levels. However, a small organization may like to implement smaller scale of Risk Values such that the visibility of risks to the senior/top management is better. At every level of Risk, a mitigation strategy is mandatory. The mitigation strategy may include extra investments or extra precautions depending upon the potential Business Impact of the risk. Some organizations may like to accept the Risks up to a certain levels because the cost to mitigate the risk is higher than the business impact. Example, an organization may like to accept risks causing a financial impact of up to $500,000 because the cost of risk mitigation may be higher than this value. Such decisions are possible after thorough "Business Impact Analysis" in various round table discussions at the top management/board level. Please be aware that business impacts are different from the asset impacts that have been analysed during the risk assessment. Business impact analytics are applied to the entire business and not only to the information assets. These decisions are critical to ensure that an accurate investment plan can be approved such that the organization does not over-invest in low critical areas or under-invest in high critical areas. The Business Impact Analysis should result in a list of Mitigation Actions that needs to be taken. Whenever an action is completed, the Risk Value can be "Normalized" to a lower value such that the impact is within acceptable limits. Examples of Mitigation actions are: addition of CCTV surveillance, better verification of visitors, visitors allowed up to visitor rooms only where CCTV cameras and microphones are installed, thorough analysis of surveillance data by security experts, offsite data storage, transition of backup tapes allowed in secured metallic boxes via Bonded Couriers, Backup system ensuring data encryption before writing on tapes, addition of clustering, fail-over, etc. to single Server installations, and so on. Although such mitigation actions can always be accomplished to reduce the Risk Values, a sound approach of keeping Risk Values in control is to have a sound Information Security Management System (ISMS) within the organization supported by Disaster Recovery Strategy, Business Continuity Planning, Service Support & Service Delivery Processes. The above description provides an overview of the concept of information risks and security management based on ISO 27005. What needs to change in the cloud computing era? This is the core research domain I am trying to propose here. To give you some ideas on the possible research opportunities, I am presenting a list of sample topics as the following. In addition to the following suggestions, please contact us at consulting@eproindia.com or consulting@eproindia.net to get more topic suggestions and to discuss your topic. We will be happy to assist you in developing your narrow research topic with an original contribution based on the research context, research problem, and the research aim, and objectives. (1) Managing the widening domain of information assets on cloud computing in the information security risk management framework. (2) Modeling dynamic attack graphs for identifying the sources of risks in cloud computing. (3) Developing an information security risk management program for cloud-hosted information assets starting from the basics. (4) Modeling attack scenarios on cloud computing for simulating controls determined through information security risk assessment. (5) Risk assessment and protection against insider threats in cloud computing. (6) An information security and risk management project plan on cloud computing detailing the tasks, efforts, timelines, resources, and dependencies. (7) ISO 27005 and COSO-based quantitative modeling of information risk management on cloud computing. (8) Developing information security metrics and measures for risk assessment on the cloud computing. (9) Vulnerability flow analysis and cause-effect relationships analysis of risks factors on the cloud computing information systems. (10) Assessing and managing platform services risks in the Platform-as-a-Service (PaaS) cloud computing model. (11) Multi-agency collaborative risk management of cloud computing information systems. (12) Analytical Hierarchy Modeling (AHM) of cloud computing risk management. (13) Risk management of Internet of Things interconnected through cloud computing for cloud-based manufacturing and supply chain management. (14) Trust relationships and privacy protection models for risk management on cloud computing. (15) Risk management of financial services and payment systems operated through cloud computing. (16) Modeling malicious activity diagrams and behavioural patterns for identifying high risk actors and their behaviours on cloud computing. (17) Assessing and managing ICT infrastructure services risks in the Infrastructure-as-a-Service (IaaS) cloud computing service model. (18) Trust and Accountability modeling for information risk management on cloud computing. (19) Information Security Risk Management in mobile communications infrastructures built upon 4G LTE and LTE Advanced technologies. (20) Managing information security in the era of mobile employees connecting to cloud-based organisational ICT resources through ubiquitous mobile access. (21) Modeling an enterprise architecture and enterprise risk management framework on cloud computing. (22) Security policy formulation and enforcement on cloud-hosted information assets. (23) Mapping threats on the clouds with vulnerabilities of information assets on cloud computing following the NIST SP 800-144 guidelines, and the ISO 27005 and ISO 27017 standards. (24) A study of COBIT 5 for risk management on the cloud computing. (25) Comprehensive controls application based on risk assessment on cloud computing using the Cloud Controls Matrix by the Cloud Security Alliance. (26) The emerging culture of security awareness and compliance in companies facing the concerns and challenges related to risk management of cloud-based information assets. (27) A review of client-side controls for securing cloud-hosted information assets in the Amazon Web Services (AWS) framework. (28) Managing risks of information assets created and managed through Amazon Web Services (AWS) framework. (29) A review of risks facing the global DNS servers seeding the cloud computing services and their possible mitigation strategies. (30) Standardising the risk management vocabulary and the ISO 31000:2009 standard. (31) A model of systemic, structured, and timely risk assessment on the cloud computing using intelligence from the dynamic security agents and the Virtual Machine Monitors (VMMs). (32) Tailoring guidelines for risk evaluation and treatment analysis for cloud-hosted ICT assets. (33) Training, awareness, and security indoctrination for mobile employees accessing cloud-hosted ICT resources through ubiquitous mobile computing. (34) Managing security risks through cloud-based De-militarized Zones (DMZ) for protecting Virtual Private Clouds. (35) Modeling risk assessment data collection from distributed tacit knowledge sources for identifying the complex relationships among cloud-based information assets. (36) Identifying attack patterns and attack scenarios on cloud computing through distributed intelligent agents moving randomly in a cloud computing virtual infrastructure. (37) Structural relationship causal modeling of threats in cloud computing and assessing controls application (38) Embedding risk awareness in business process modeling and engineering on the cloud computing (39) Network graph analysis with probabilistic relationships for assessing threat scenarios on cloud computing (40) Deploying distributed firewalls and intrusion detection and prevention systems on cloud computing for managing virtualisation risks We will be happy to assist you in developing your narrow research topic with an original contribution based on the research context, research problem, and the research aim, and objectives. Please contact us at consulting@eproindia.com or consulting@eproindia.net to discuss your topic or to get ideas about new topics pertaining to your subject area. We will be happy to assist you in developing your narrow research topic with an original contribution based on the research context, research problem, and the research aim, and objectives. Further, We also offer you to develop the "problem description and statement", "aim, objectives, research questions", "design of methodology and methods", and "15 to 25 most relevant citations per topic" for three topics of your choice of research areas at a nominal fee. Such a synopsis shall help you in focussing, critically thinking, discussing with your reviewer, and developing your research proposal. To avail this service, Please Click Here for more details. Previous Article Next Article Copyright 2023 - 2026 EPRO INDIA. All Rights Reserved |